

Ah, yes, just over five attempts for every human alive. I assume they took the reply addresses at face value and have forwarded 45 billion cease & desist letters to Microsoft’s Redmond office?
 Inbred: chaorace’s family has been a bit too familiar. (Can be inherited)
Inbred: chaorace’s family has been a bit too familiar. (Can be inherited)




Ah, yes, just over five attempts for every human alive. I assume they took the reply addresses at face value and have forwarded 45 billion cease & desist letters to Microsoft’s Redmond office?


Could have been MMANAA 😔
If you hate job boards then you need to find individual company “Careers” pages and go from there.
How you go about this varies a lot by skillset and industry, but I’ll just throw out a random example: lots of Linux jobs exist in the DevOps space (think Kubernetes, Ansible, Chef, NixOps). It just so happens that lots of medium-sized software companies need DevOps people, so you can pretty easily find companies looking for DevOps hires just by browsing Y Combinator’s Startup Directory
With that being said, I get the impression from the way your post is worded that you’re looking to break into a new career without having yet established a concrete plan. My advice would be to step back and consider specific options first. Almost all jobs like these require industry-specific certifications (e.g.: CompTIA, ITIL, AWS, Azure, Cisco, etc.). You need to look at your options, pick a certification, earn it, then go job hunting. Certifications are great for securing entry level jobs and the standards body issuing these will often provide an online directory of partner companies who are currently hiring.
You’ll understand when you’re older, son


Ugh… they got Plasma everywhere!


You the real MVP 👑


This was, without any doubt, a prophetic dream. The apocalypse will soon be upon us! Be wary of the four horsemen: Ronald, King, Wendy, and… Chihuahua
Try Satty? It’s inspired by flameshot, Wayland native, and written in Rust.


Nice. Flagship features like these so often feel overlooked in the Linux GPU discussion. I like to think that’s because we’re all very serious pragmatists who don’t care for such frivolous addons, even if the simple truth is that vendors are indifferent towards Linux as an end-user platform.
In light of that, features like these coming in with 1st-party support is a welcome sign that things are (slowly) changing. Emphasis on “slow”; I don’t find it terribly impressive that Nvidia’s partially reversed the proprietary own-goal which they call NVAPI, especially considering the still ongoing parade of new (also proprietary!) standards which they insist on shoehorning into it… but I’ll acknowledge that they’re making progress nevertheless 😤


Yeah, I’m subscribed to notifications for the PR and have been holding out waiting for it to get merged because it’s easier to maintain a clean git history that way. If the PR’s still not merged by this evening I’ll just bite the bullet and do it the (slightly) harder way for the sake of staying current with the new seasonals


Male A to Male C is abolutely possible. It’s the Male A to Female C adapters which are evil. There is no pinout mapping that will turn an A host into a “real” C host and that’s exactly what a Male A to Female C adapter purports to do.
In any case, if you know what you’re doing then all bets are off the table. Hack away freely because at the end of the day it’s all just copper and bits anyway. With that being said, anyone who knows what they’re doing does not require my permission to… vague gesture know what they’re doing.


Like I said: in order to do it the non-evil way you need to cram in an onboard USB chip. Female USB-C from a Male USB-A plug-in is explicitly not possible to implement in a spec-compliant manner because of the pinouts.
You can brute-force a smaller passive adapter like those online but it’s a devil’s bargain. Nobody targets these janky adapters when designing products. USB-C things will just break without any rhyme or reason because you’re fundamentally breaking the hardware contract and “lying” about the capabilities of your port.


No, it’s because I read an expert opinion on the subject: https://old.reddit.com/r/UsbCHardware/comments/m7rcu5/any_reliable_usbc_female_to_usba_male_adapters_yet/grducjr/
If you hate Amazon you can buy it on the CableCreation website instead.
EDIT: that monoprice adapter isn’t even active lol!
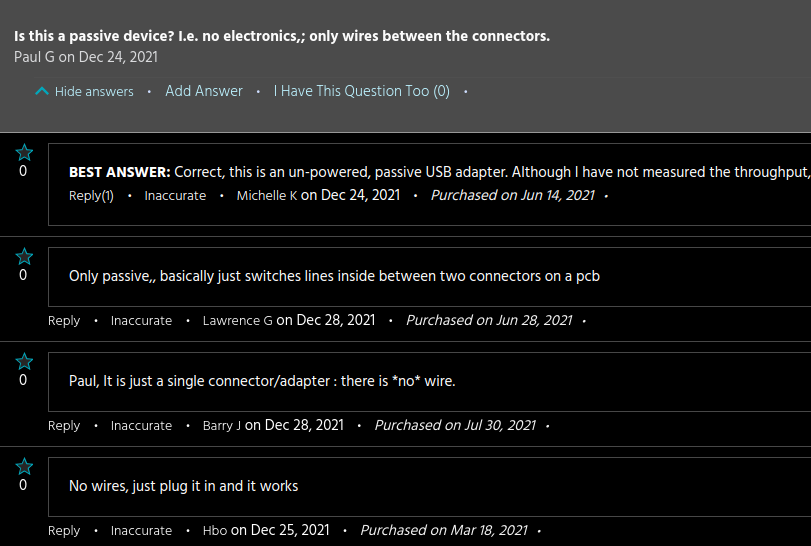


First thing’s first: all such adapters should be considered evil by default. The only way to make a compliant adapter is with active circuitry in the adapter essentially providing an entirely standalone USB controller interface.
With that being said, here’s an adapter which does exactly that. Back when I researched this topic in October I found that the linked adapter is essentially the only one of its kind on the market right now.
I am of two minds:
It’s a mess, but honestly so are a lot of critical FOSS projects (e.g.: OpenSSH, GNUPG, sudo). Curmudgeons gonna curmudgeon. There was a point of no return and that was years ago – now that Wayland’s finally becoming useable despite itself it’s probably time to come to terms with the fact that better alternatives would have arisen had anyone thought they could truly manage it.


No, I am not contradicting myself. Let me say it again with the ambiguity removed:
I’m sure you still believe this is a load of apologia and frankly you can think what you want, but you should probably know that I’d already read about the Cox story when it first broke and specifically chose my words with that knowledge in mind.


Read the document:
The growing ability to access microphone data on devices like smartphones and tablets enables our technology partner to aggregate and analyze voice data during pre-purchase conversations.
Key word is “technology partner”. They’re buying voice transcripts ripped from someone else’s spyware and selling the service of scraping it for keywords and maybe somehow tying that back to an individual by cross-referencing the hit against data from traditional above-board ad platforms.
Google isn’t buying transcripts, Facebook isn’t buying transcripts. It’s Cox Media buying shady recordings stolen from spyware-compromised devices and then trying to whitewash it into something sellable with their (unverifiable) cross-analytics middleware.


Hmm… what’s the purpose of loading amdgpu at all if you’re using an NVIDIA card? Optimus?


we still have people that do not believe that the phones are always listening when seemingly any website or app you use gives you advertisements about what you were just talking about in the other room with the phone locked.
Oh come on. Don’t bring this into conspiracy territory. Yes, eavesdropping does happen, but it’s not something an uncompromised Android phone will do when locked. Even when it does happen in the case of spyware, the people doing it aren’t selling your transcriptions to advertisers.
People should still opt out of as many of GAPS’s spyware-like features as possible, as you suggest, but not because it’s a special anti-listening-device warding spell.
You may be interested in reading this post about the process of packaging Steam.
tl;dr: It’s mostly an annoyance reserved for packagers to deal with. Dynamically linked executables can be patched in a fairly universal fashion to work without FHS, so that’s the go-to approach. If the executable is statically linked, the package may have to ship a source patch instead. If the executable is statically linked & close-source, the packagers are forced to resort to simulating an FHS environment via chroot.